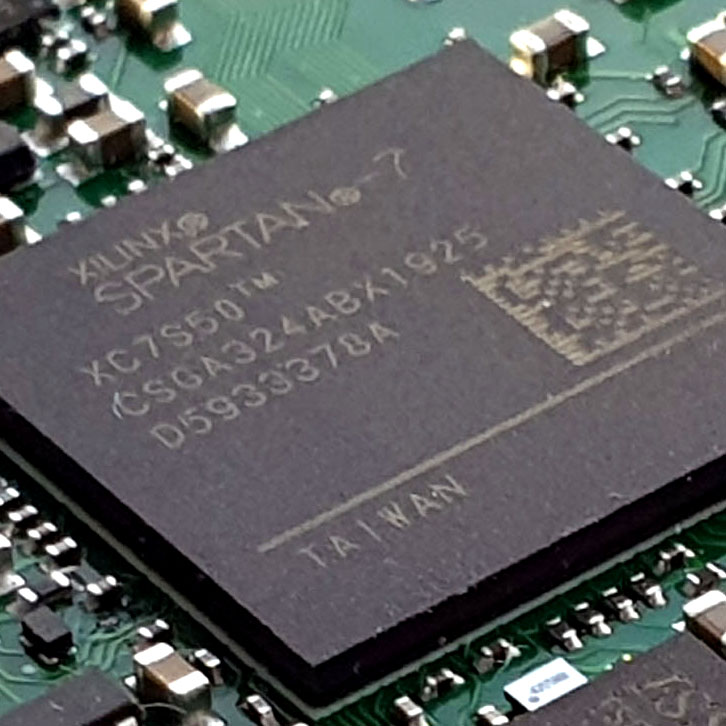
Betrusted is an initiative to put you in control of your secrets. No ads. No AIs. No mysterious hardware black boxes. Nothing between you, the math, and the immutable laws of physics: Betrusted is full-stack transparency, purpose-built to facilitate inspection and audit. We aim to provide the smallest set of features necessary to keep end-to-end secrets, while providing safe, user-friendly defaults for everyday use.
Betrusted's scope extends from silicon to user software. It is realized in a series of open source projects, each one tackling a different part of the stack.
Our Core Principles
Betrusted is designed around the principles of transparency, simplicity, completeness, and self-sealing.
Transparency
Transparency is the bedrock of trust. Understanding what makes a thing tick gives us an evidence-based reason to trust that it works as intended. Betrusted is unique in that instead of a black-box CPU chip, we start with inspectable, open-RTL CPU cores, delivered in the form of an FPGA or an IRIS-inspectable chip. This means you no longer have to accept on faith that a black epoxy rectangle contains precisely the circuits it advertises.
Simplicity
Simplicity addresses the reality of only having 24 hours in a day. Even though the full source code for the Linux kernel and Firefox is published, nobody has the time to personally review every release for potential security problems; we simply trust that others have done a good job, because we have no other choice. Betrusted is a platform powerful enough to be useful for single tasks, while simple enough that individuals or small teams could build it from scratch. But don’t worry, despite its simplicity, Betrusted’s computational capability is sufficient for core security tasks such as authentication, instant messaging, and even end-to-end encrypted voice calls.
Completeness
Trust should begin at your fingertips and end at your eyes. Screen grabbers and keyboard loggers mean that chip-only trust solutions, such as TPMs, TEEs, and secure enclaves are insufficient; we need a complete, end-to-end solution. Private keys are not the same as our private matters, and until we can encrypt data directly to and from our brains, the “analog hole” will be a real problem. Betrusted includes the complete loop of components from the keyboard to the display. They are curated for transparency and simplicity, thus minimizing the attack surfaces that cannot be cryptographically secured.
Self-sealing
“Three can keep a secret, if two of them are dead”. As Benjamin Franklin acutely observed, relying on trusted third parties to provision our keys is imprudent: self-sealing is the only way to keep a secret. Betrusted requires no special tools, NDAs, or third-party expertise to provision the system with secrets: it can generate and seal its own private keys on-chip in a transparent and open manner.
Documentation & Support
- The betrusted wiki aggregates all the technical documentation for the platform.
- The Precursor Matrix Space is the channel to reach live humans for questions & answers.
- The Xous Book is a deep-dive into the kernel architecture.
- The main betrusted github repository is the place to hunt for anything you didn’t find at the link above.
- The IRIS link tree aggregates all the published information on IRIS.
Media
- Video: 39C3 Xous and Baochip
- Video: 38C3 Introduction to IRIS
- Video: 36C3 Introducing the core principles that motivate the hardware architecture
- Video: LCA20 Evolution and planning of the overall project, including software layers
- Video: FOSSNORTH20 Precursor overview talk
- Blog: Precursor SoC Tour
- Blog: Precursor Mainboard tour
- Blog: Other Precursor posts hardware security evaluation, braille keyboard, hackability, mechanical and PCB design aspects.
- Blog: Precursor + Renode
Other Tech Morsels
- Avalanche Noise Source design notes
- Curve25519 Engine documentation
Who is behind betrusted?
The betrusted-io github repository’s people page lists the developers that have elected to reveal their participation publicly.
The administrative contact for the betrusted.io project is Andrew ‘bunnie’ Huang (@bunnie.org bluesky/@bunnie masto/blog).


The Betrusted team is funded in part through the NGI0 PET Fund, a fund established by NLnet with financial support from the European Commission’s Next Generation Internet programme, under the aegis of DG Communications Networks, Content and Technology under grant agreement No 825310.